dotfuscator how to check code is obfuscated
I obfuscate the exe file without changing anything in settings leaving the defaults. 2 Obfuscating can be done on a folder directly meaning all the javascript files in the folder will be obfuscated.

What Is Obfuscation Preemptive
When I run the application I notice that something does not work.
. Ensure that your build saves the obfuscated output assemblies and the renaming map file as build artifacts eg. Obfuscate control flow using Dotfuscator then again control flow obfuscate the obfuscated exe using NET Reactor or Crypto Obfuscator. Dotfuscator works with all flavors of NET including Xamarin NET Core NET 5 ASPNET and UWP apps.
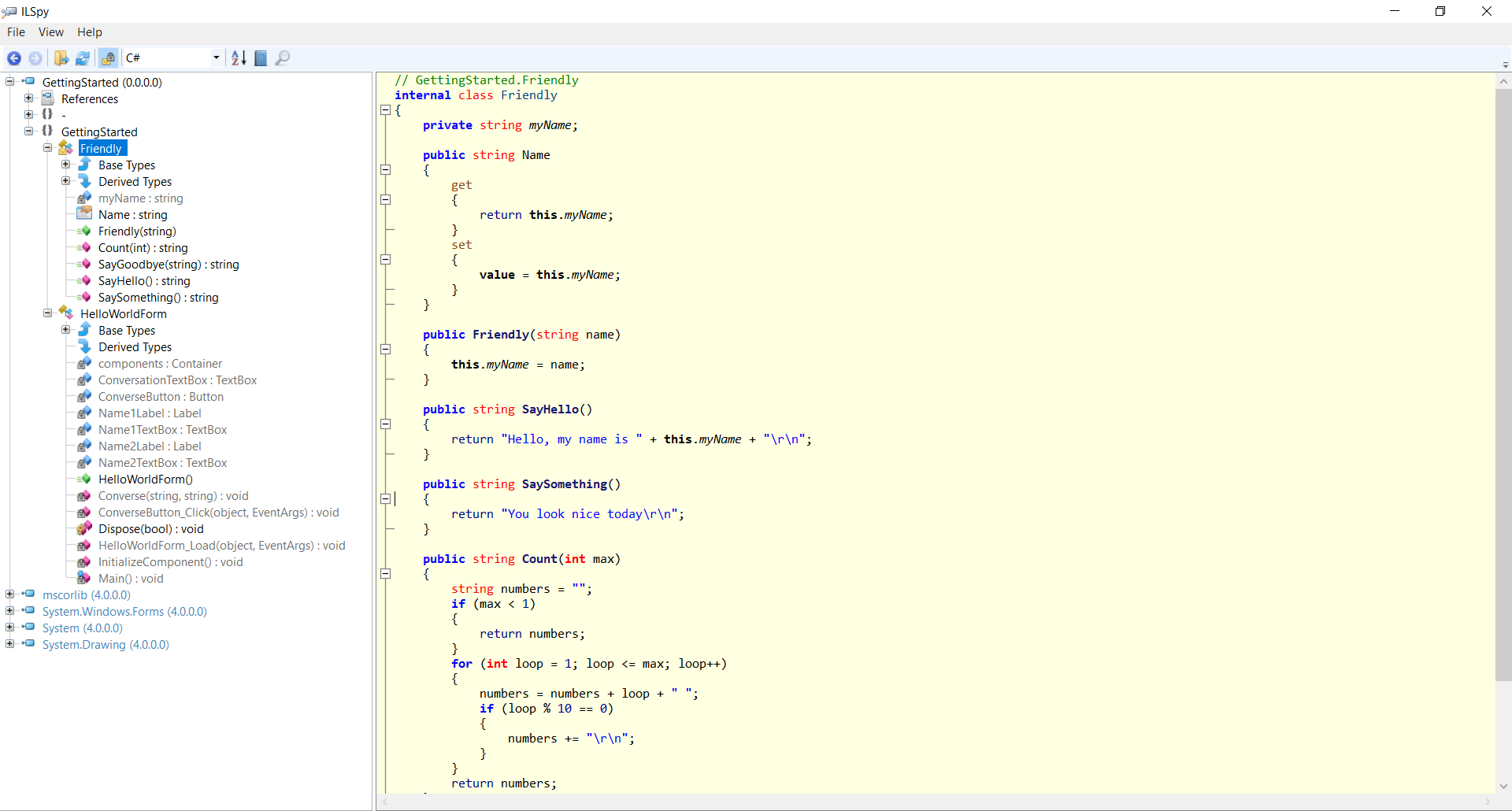
The blue diamond shaped icons indicates that they are renamed methods and fields. If I revert back to my old DLLs fo my precompiled website it works fine. Under Code tools check the PreEmptive Protection - Dotfuscator item.
3 Although this works perfectly in obfuscating the files the files are not replaced. Why is my obfuscated code larger than my original source. Also strings are converted to xAB hexadecimal code to make things a little bit harder to understand.
Just remember any obfuscation is better than no obfuscation. Dotfuscator is a NET Obfuscator and In-App Protection solution that helps companies with apps worth protecting secure trade secrets IP reduce piracycounterfeiting and protect against tampering and unauthorized debugging. Configure any further installation settings as appropriate for your environment.
For companies or individuals that really need extra protection the professional edition of Dotfuscator will provide much more code protection. ConsoleWriteLine Returns 0 if not obfuscated 1 if obfuscated. In addition to adding code constructs Dotfuscator works by destroying the code patterns that decompilers use to recreate source code.
Create a ConfuserEx project file using the ConfuserEx template file. It is recommended to check it into source control. Obfuscation using DotFuscator.
Dotfuscator employs advanced control flow obfuscation. On the filesystem notice the new DotfuscatorReports directory in your projects directory. Dotfuscator is the obfuscation tool that ships with Visual Studio 2012.
What about porting specific non-trivial functions over to a language like C and obfuscate that. Here theres an example. When ready to install Visual Studio click the Install button.
How does code obfuscation work. So what I would suggest its to check if in the code youre analyzing theres some some obfuscation specific transformations patterns. The Provision task exposes a build variable with Dotfuscator Communitys location on the build host.
Your C program could then use reflection to make calls to this externalunmanaged dll. In addition to reverse-engineering bad actors may attempt to pirate your application alter the applications behavior at run time or manipulate data. When I deploy these obfuscated DLLs on the webserver my site doesnt work.
After this if I de-obfuscate the exe the code can not be understood by any intermediate level programmer. In the Quick Release outcomes revealed under the Menus heading choose Tools PreEmptive Defense Dotfuscator Neighborhood. The ability to add.
Dotfuscator is a product of PreEmptive that makes NET application more difficult to be reverse engineered tampered and unauthorized debugging which includes Xamarin Forms. Obfuscate the projects assembly and store the obfuscated assembly in the Confused directory. Most of the times they crash while trying to do so.
The name of the package is JavaScript obfuscator. When doing control flow obfuscation on your code Crypto Obfuscator changes the structure of your code into spaghetti code while maintaining 100 the logic and output of the code. You can use the Protect task to invoke Dotfuscator Community as a distinct step in your build definition.
The result is that decompilers are unable to reconstruct your code and output incorrect or garbage code. Otherwise the exe without any obfuscation works correctly. Dotfuscator can obfuscate your NET assemblies to hinder reverse-engineering while maintaining original application behavior.
In this tutorial we are going to. Because the obfuscator introduces new pieces of code that are meant to protect and defend against debugging and reverse-engineering. I used DotFuscator Community edition that ships with VS2005 to obfuscate some of the DLLs from my PreCompiled website.
The end result is code that is semantically equivalent to the original but contains no clues as to how the code was originally written. Release Microsoft Visual Studio. The assembly is obfuscated by calling the PowerShell script ObfuscateAssemblyps1.
Here is the gist of the window in which code breaks. Dotfuscator can be configured in a separate GUI application via command line settings or added a project to your VS solution. In the Quick Release Ctrl Q search bar type dotfuscator.
Now to avoid reverse engineering I am using Dotfuscator embedded in VS2012. You dont have to worry too much about code size. Via a Copy Files task.
To start utilizing the Dotfuscator Neighborhood interface follow these actions. The main steps in the obfuscation workflow are. They only need to be discoverable by the same probing rules used by Dotfuscator to locate referenced assemblies.
This is the Dotfuscator config file which tells Dotfuscator how to obfuscate your code. Therefore an independent developer can easily provide a basic layer of obfuscation to their code without having to fork out any money. Once the assembly is selected hit Ctrl B or go to Build Build Project Click on the Results tab and expand the root tree and the sub-trees.
When performing a run using incremental obfuscation Dotfuscator must have access to all the applications assemblies although it is not required that all the assemblies be included in the config. The Summary panel displays PreEmptive Protection - Dotfuscator under the Individual Components section. 1 There is an npm package for obfuscating the javascript code.
Returns 0 if not obfuscated 1 if obfuscated -1 if error. STAThread static int Main string args if argsLength 1 ConsoleWriteLine Usage. This directory contains information about how the project was obfuscated including how to reverse the renaming process.
Once the obfuscation process is completed you can examine the obfuscated assembly using ILDASM. Its also important to protect the integrity of your application. The way to secure this is generally to put this stuff into a webservice but you said you couldnt really do that.
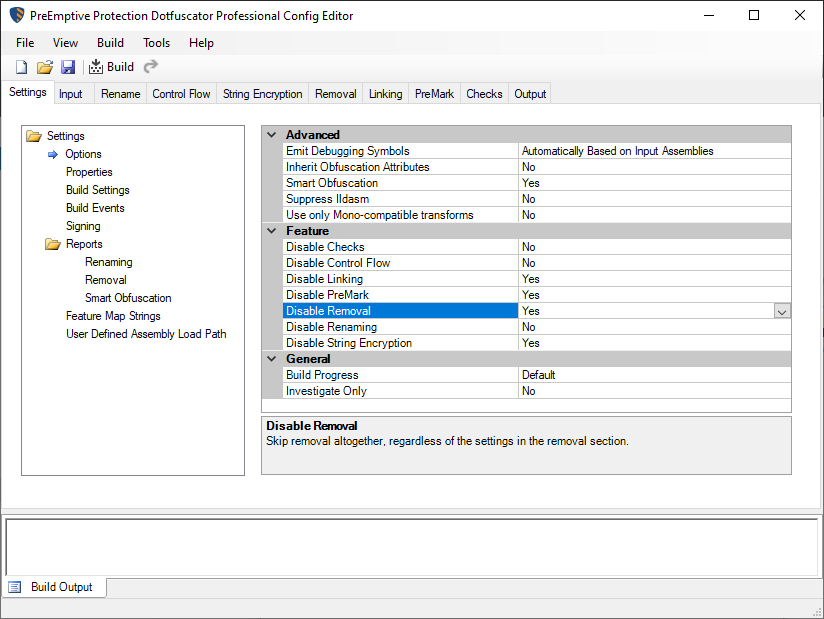
Reverse Engineering Dotfuscator Professional 6 4

Enhance Protection Dotfuscator Professional 6 4
Renaming Dotfuscator Professional 6 4

What Is Obfuscation Preemptive
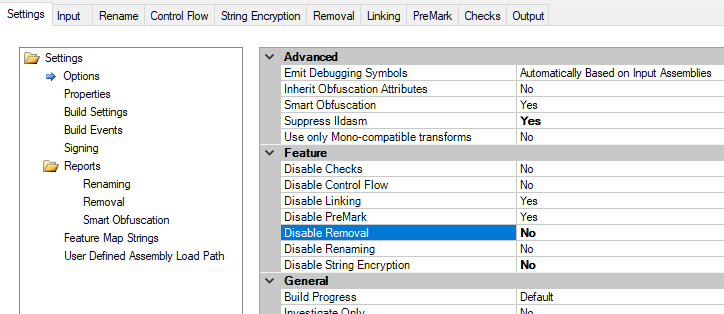
Enhance Protection Dotfuscator Professional 6 4

Net Goodies Obfuscation With Dotfuscator

The Config Editor Dotfuscator Professional 6 4
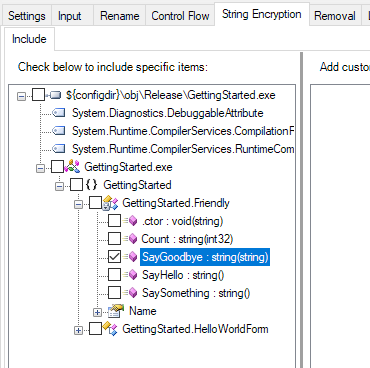
Enhance Protection Dotfuscator Professional 6 4

Understanding Checks Dotfuscator Professional 6 4
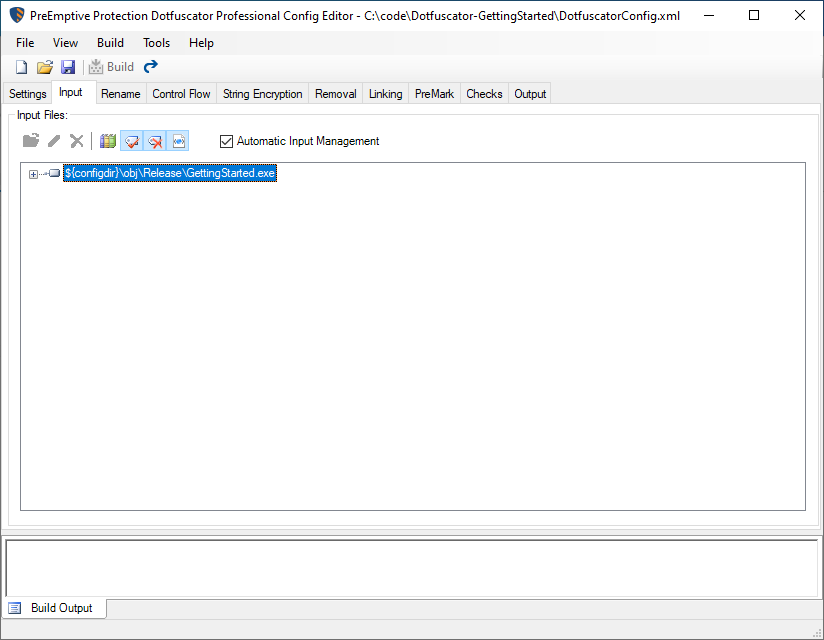
Enhance Protection Dotfuscator Professional 6 4

What Is Obfuscation Preemptive
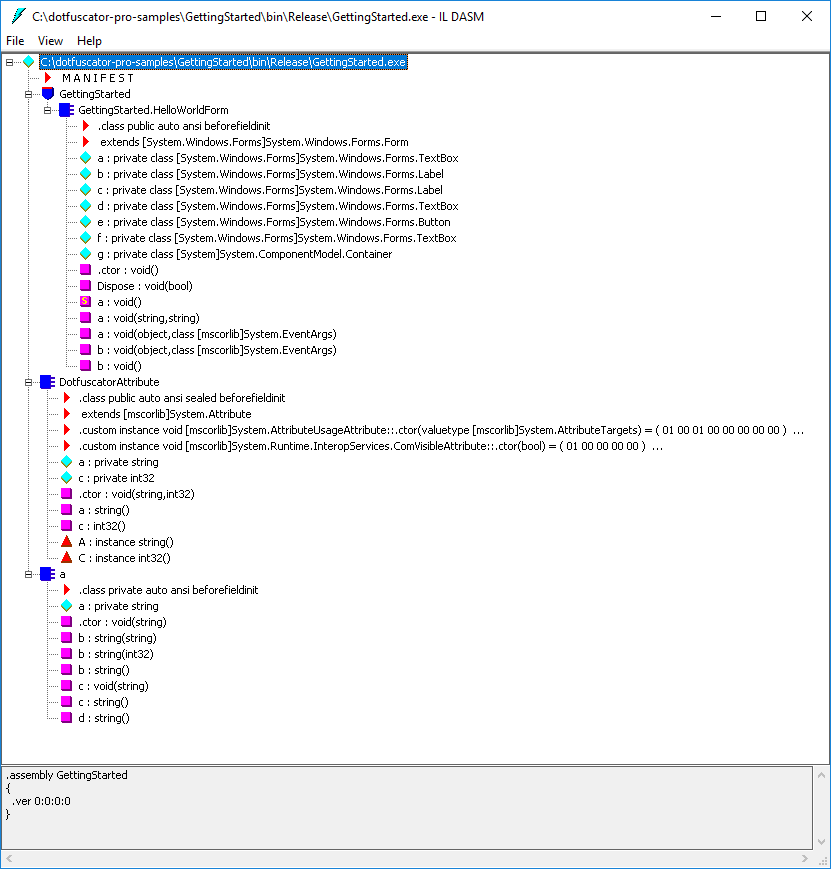
Reverse Engineering Dotfuscator Professional 6 4
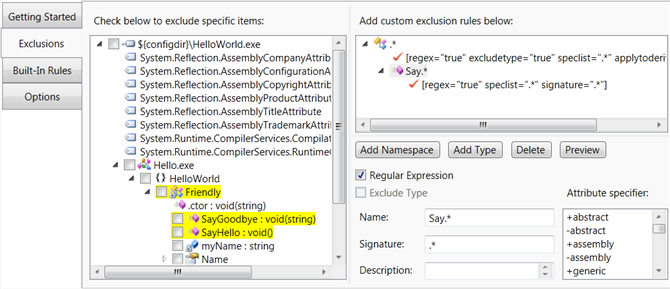
Renaming Configuration Dotfuscator Community User Guide 6 3
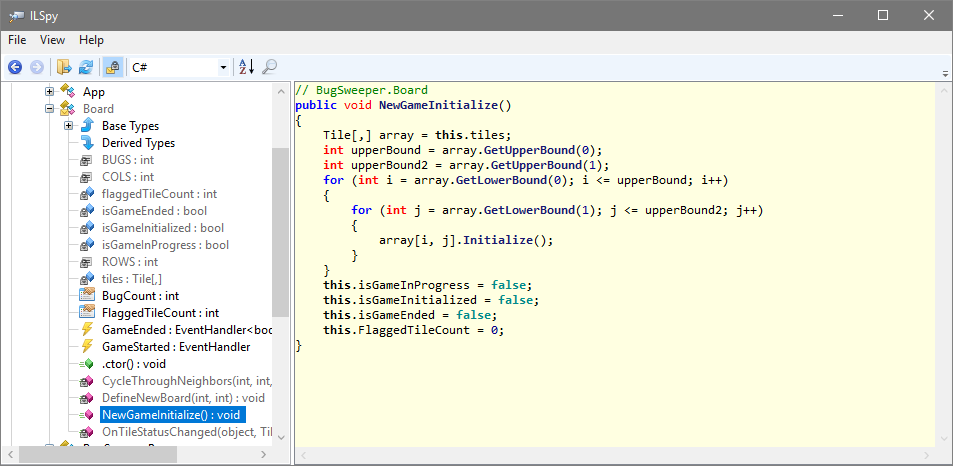
Reverse Engineering Dotfuscator Professional 6 4
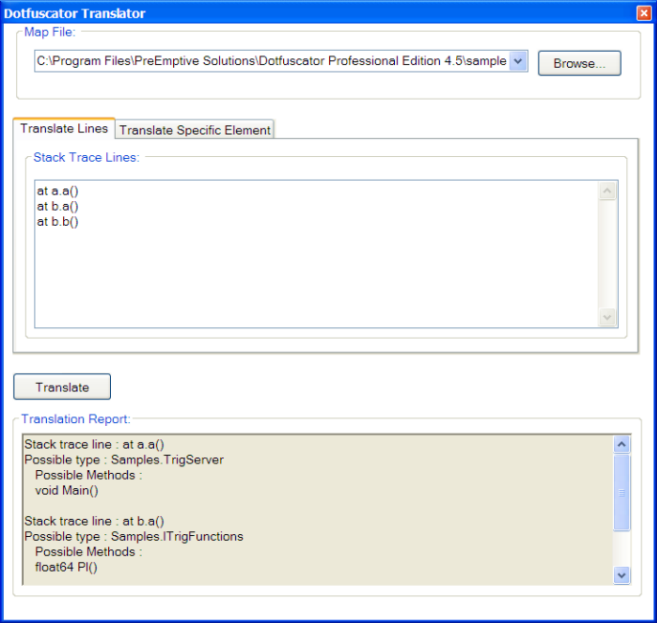
Decoding Obfuscated Stack Traces Dotfuscator Professional 6 4

Renaming Dotfuscator Professional 6 4

Vb Net Obfuscation Automation By Using Post Build Commands In Visual Studio Stack Overflow

Renaming Dotfuscator Professional 6 4
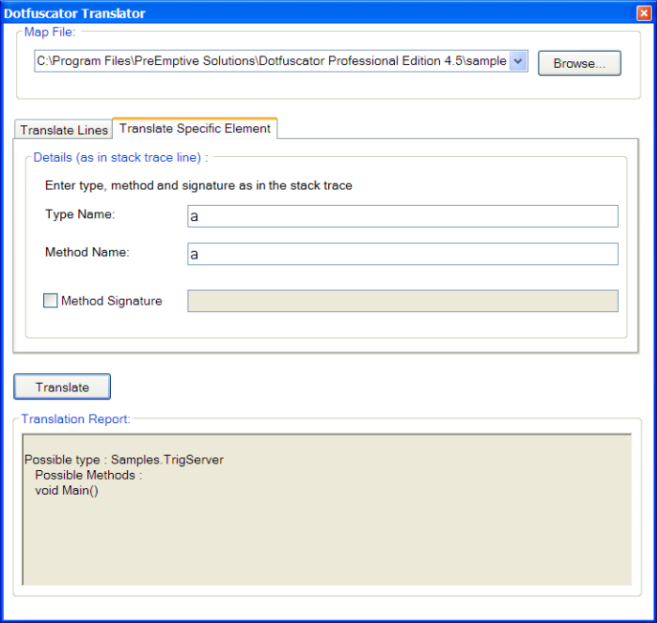
Decoding Obfuscated Stack Traces Dotfuscator Professional 6 4
Comments
Post a Comment